The Sender Policy Framework: Bare Bone Essentials
Background
Email is part of our daily lives; everyone who works in an organization or uses the internet frequently has opened an email account at least once in their lifetime. But this technology, invented in the 90s, wasn’t created for widespread use and was not designed with security in mind. This makes impersonation easy, and that was why a protocol such as SPF was developed.
SPF is an email authentication protocol designed to combat email address forgery, also called spoofing. Attackers use spoofing to disguise their emails so that recipients think the email is coming from a legitimate source. SPF allows administrators to publish hosts in their DNS TXT records, specifying which hosts can send email from that domain. SPF is just one of several email authentication mechanisms. Other mechanisms, such as DMARC and DKIM, are also used for authenticating email.
According to RFC 7208, SPF once had a dedicated record type, but the developers of the protocol found it easier to use TXT to implement SPF records, and the old record type was deprecated.
Example of an SPF Record
SPF record types are in-depth, and we wouldn’t be able to cover all of them here. We’ll look at a single record and break down what it means. Take a look at the record below:
v=spf1 ip4:192.0.2.0/24 include:_spf.google.com -all
v=spf1: Declares SPF version 1 (required).ip4:192.0.2.0/24: Authorizes all IPs in the192.0.2.0subnet to send mail.include:_spf.google.com: Authorizes Google’s mail servers. For instance, if sending through Google Workspace.-all: Fails any sender not explicitly listed (hard fail).
This is a straightforward example to explain how SPF works. There are certainly more complex records depending on how many sending servers are listed.
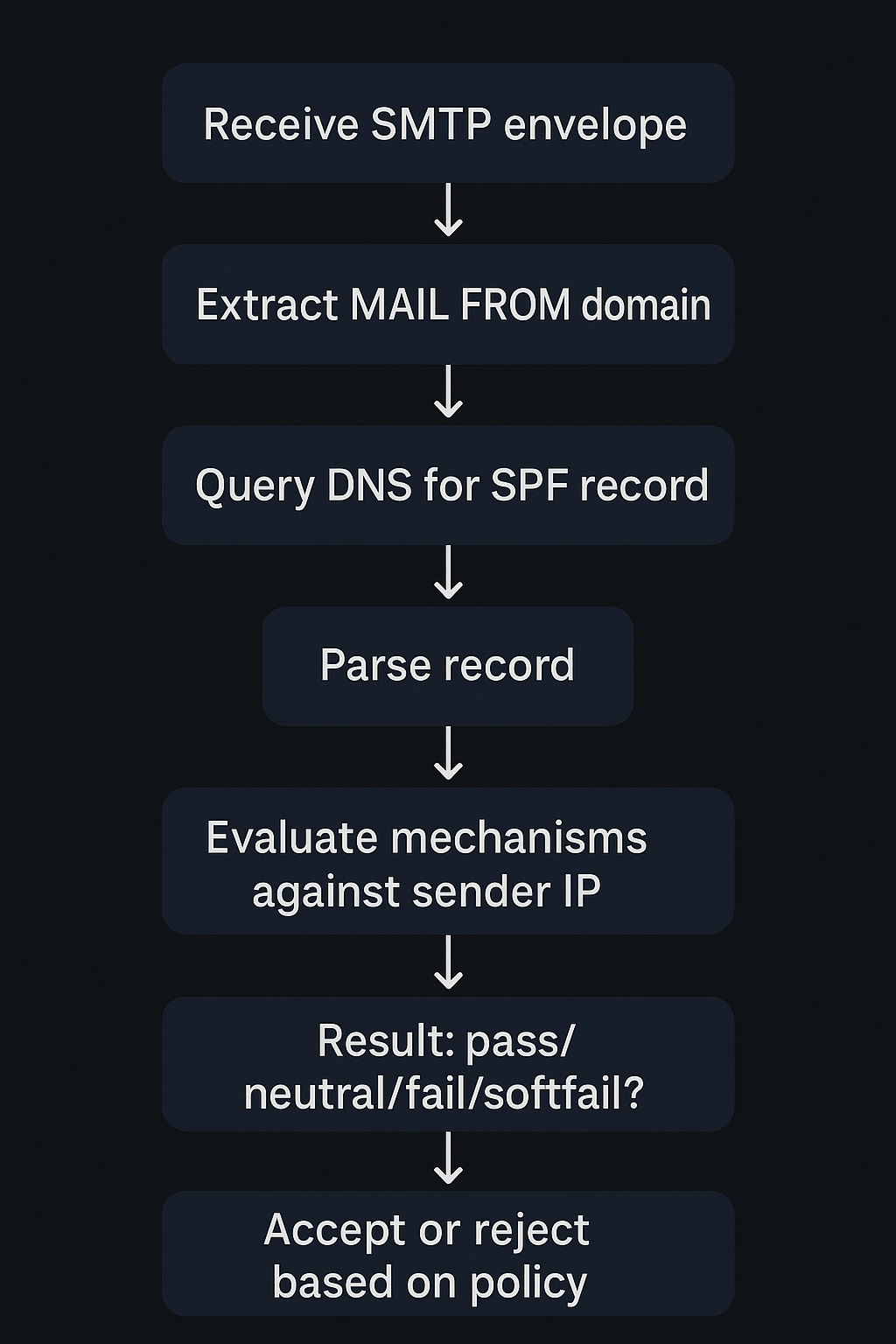
How a Receiving Mail Server Verifies SPF
This is a multistep process with lower-level granular details, but here it is at a high level:
- The server accepts the incoming connection and reads the
MAIL FROM(envelope sender) command. - It isolates the domain portion of the envelope sender address to know which domain’s SPF policy to check.
- The SPF engine performs a DNS TXT lookup for that domain, searching for a record beginning with
v=spf1. - The server parses the SPF string into its mechanisms (e.g.,
ip4,include,mx,a) and qualifiers (+,-,~,?). - Each mechanism is evaluated in order against the sender IP address.
- These steps produce an evaluation result, and based on that result, the server can either accept or reject the mail.
Here is the flow chart of the process;
Conclusion
That’s SPF at its core.
There is still more to cover and learn if we want to go down the rabbit hole.SPF is a simple, DNS-based way to make
impersonation harder.
It’s free to implement.
By publishing an accuratev=spf1record, you take the first step toward protecting your domain from spoofed mail.
Remember, SPF alone won’t stop every phishing or spoofing attempt, so it works best in concert with DKIM and DMARC.
Once your SPF record is live,
monitor it regularly (using tools or scripts) and update it whenever you add or remove sending services.
A well-maintained SPF policy lays the groundwork for a stronger, more reliable email ecosystem.